Security becomes more and more a topic that receives the level of attention it deserves. For long security has been a topic that has commonly been seen something that, the other department for sure is handling. More and more security is becoming engraned in every level of IT departments and business organizations.
Companies start to realize that security is a subject that should be the foundation of the enterprise architecture and not something you add on top at a later stage and you do just a bit. Architects, developers and administrators as well as business and IT management becomes aware that ensuring the right level of security is vital for surviving and crucial to ensure day to day operations are not hindered in any way or form.
When thinking about security most people think about firewalls, antivirus solutions and passwords… overlooked are commonly the security parts needed in the developed code, how to secure a database and ensuring the operating system used on your servers is configured in the most optimal and secure manner.
Operating system security
Operating systems, and Linux is not any different in that, are still too often installed in a next, next finish manner. Not looking at how you should secure your installation correctly. Ensuring you have the correct level of hardening on your Oracle Linux system is vital to ensure full end-to-end security of your IT footprint.
CIS Benchmark
Good documentation and guidance on how to do proper hardening of your Oracle Linux Operating system is provided by both Oracle and CIS. CIS provides a benchmark guideline on what needs to be in place to ensure a proper secured Oracle Linux installation. CIS Oracle Linux 7 Benchmark, provides prescriptive guidance for establishing a secure configuration posture for Oracle Linux version 7.0.
By default the installation Oracle provides is already secured up to a certain level without the need to undertake any specific actions. Ensuring the CIS benchmark guidelines are implemented will ensure an even higher level implementing security on your Oracle Linux system
Additionally, the CIS benchmark is a well respected and accepted hardening guideline. Implementing it and scoring the level of implementation will give you a good insight in how your hardening scores against industry standards.
Automate it all
With the changing IT world into a model where automation is being implemented as much as possible and providing end-users with a self-service options to request and provision new systems. Using automation can support in creating a more secure implementation of Oracle Linux operating systems.
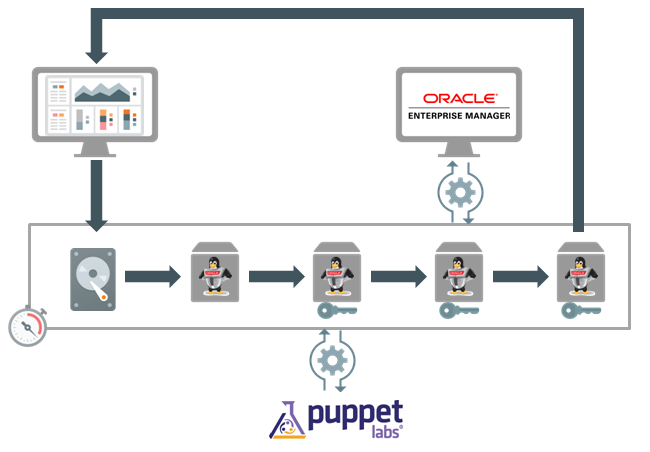
In the below shown flow you see how a new environment is requested, build and delivered to the requester for use. Requesting can be done, for example, via Oracle Enterprise Manager self service however, can also be done via the Oracle Cloud portal or any other form of self service portal.
In the above diagram the following steps are undertaken:
As you can see from the above steps, you can have a fully automated deployment which will ensure a fully secured and hardened Oracle Linux implementation is provided to the end users. At the same time the newly created machine is registered with Oracle Enterprise manager. Next to the well know use of Oracle Enterprise Manager to monitor performance and availability of a machine and do maintenance tasks it provides the option to use to compliancy framework. The compliancy framework within Oracle Enterprise Manager can be used in real-time to monitor the setting of the machine and benchmark them against a defined security standard. The benefit of this is that you can have a realtime insight in the level of implemented security over your entire IT footprint and produce compliancy reports and exception reports with the push of a button.
The use of Puppet is something seen more and more in environments that use a high level of automation. Puppet will be able to push configurations to all environments without the need to have human administrators taking the burden of doing manual tasks in the final configuration of machines. When building an automated deployment flow you do not want to include every setting in your golden machine image, the final configuration is something you would rather do with a solution like Puppet. Puppet is not alone in the market, other solutions are available such a Chef, Ansible and Salt however Puppet is currently the most commonly used solution.
Implementing a solution as shown above provides you a full end-to-end automation of new environments and at the same time makes the outcome of the process more predicatively and more secure.
Companies start to realize that security is a subject that should be the foundation of the enterprise architecture and not something you add on top at a later stage and you do just a bit. Architects, developers and administrators as well as business and IT management becomes aware that ensuring the right level of security is vital for surviving and crucial to ensure day to day operations are not hindered in any way or form.
When thinking about security most people think about firewalls, antivirus solutions and passwords… overlooked are commonly the security parts needed in the developed code, how to secure a database and ensuring the operating system used on your servers is configured in the most optimal and secure manner.
Operating system security
Operating systems, and Linux is not any different in that, are still too often installed in a next, next finish manner. Not looking at how you should secure your installation correctly. Ensuring you have the correct level of hardening on your Oracle Linux system is vital to ensure full end-to-end security of your IT footprint.
CIS Benchmark
Good documentation and guidance on how to do proper hardening of your Oracle Linux Operating system is provided by both Oracle and CIS. CIS provides a benchmark guideline on what needs to be in place to ensure a proper secured Oracle Linux installation. CIS Oracle Linux 7 Benchmark, provides prescriptive guidance for establishing a secure configuration posture for Oracle Linux version 7.0.
By default the installation Oracle provides is already secured up to a certain level without the need to undertake any specific actions. Ensuring the CIS benchmark guidelines are implemented will ensure an even higher level implementing security on your Oracle Linux system
Additionally, the CIS benchmark is a well respected and accepted hardening guideline. Implementing it and scoring the level of implementation will give you a good insight in how your hardening scores against industry standards.
Automate it all
With the changing IT world into a model where automation is being implemented as much as possible and providing end-users with a self-service options to request and provision new systems. Using automation can support in creating a more secure implementation of Oracle Linux operating systems.
In the below shown flow you see how a new environment is requested, build and delivered to the requester for use. Requesting can be done, for example, via Oracle Enterprise Manager self service however, can also be done via the Oracle Cloud portal or any other form of self service portal.
In the above diagram the following steps are undertaken:
- The user requests a new system via a self service portal
- A standard golden machine image is used to build an Oracle Linux instance.
- The resulting virtual machine is hardened by default and includes all standard hardening rules and settings as defined in the golden machine image.
- The new virtual machine registers itself with Puppet and Puppet will implement all additional security measures needed for a deployment to make it truly safe
- The new virtual machine registers itself with Oracle Enterprise Manager. Oracle Enterprise Manager will use the compliancy framework options to monitor and report on the level of compliancy against the security baseline defined.
- The automation layer reports back to the user that the machine is ready for use.
As you can see from the above steps, you can have a fully automated deployment which will ensure a fully secured and hardened Oracle Linux implementation is provided to the end users. At the same time the newly created machine is registered with Oracle Enterprise manager. Next to the well know use of Oracle Enterprise Manager to monitor performance and availability of a machine and do maintenance tasks it provides the option to use to compliancy framework. The compliancy framework within Oracle Enterprise Manager can be used in real-time to monitor the setting of the machine and benchmark them against a defined security standard. The benefit of this is that you can have a realtime insight in the level of implemented security over your entire IT footprint and produce compliancy reports and exception reports with the push of a button.
The use of Puppet is something seen more and more in environments that use a high level of automation. Puppet will be able to push configurations to all environments without the need to have human administrators taking the burden of doing manual tasks in the final configuration of machines. When building an automated deployment flow you do not want to include every setting in your golden machine image, the final configuration is something you would rather do with a solution like Puppet. Puppet is not alone in the market, other solutions are available such a Chef, Ansible and Salt however Puppet is currently the most commonly used solution.
Implementing a solution as shown above provides you a full end-to-end automation of new environments and at the same time makes the outcome of the process more predicatively and more secure.
No comments:
Post a Comment