To protect the database from attempts to hack it in a number of ways commonly a network firewall is implemented to ensure attackers cannot connect to the system running the database on ports other then intended and not from computers that should not be able to connect to the database. This way, as is the traditional and common way, is protecting the database in quite a good fashion however is not protecting it against all risks. If a server who is eligible to connect to the database is compromised an attacker could use this as a stepping stone to execute queries against the database or cause other havoc.
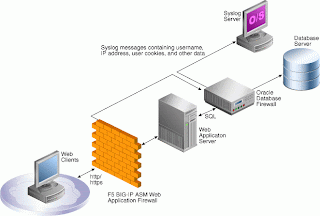
For this reason Oracle has created the the Oracle database firewall. When you deploy and Oracle database firewall your application server is no longer talking directly to your database however to the firewall. Based upon a whitelist or blacklist principle certain statements are allowed to be send to the database. Statements that are not allowed are dropped. having such a solution in place is adding an extra layer of security to your design. An diagram showing such an implementation is shown below.
A less known fact about the Oracle database firewall is however that it can be integrated with other security products from other vendors. F5 for example is providing a solution with the BIG-IP ASM (Application Security Manager) which is is an application layer firewall specially designed to recognise attacks on an application layer level. In most common attacks for systems where you would deploy an Oracle database firewall you will have an application layer which might only be protected by a network firewall. In a solution where you also deploy a application layer firewall you will gain an extra level of security.
The BIG-IP ASM solution is able to detect and block an attack on the application layer and next to this forward this information also to the Oracle database firewall. This has a number of advantages. First of all the attack context is communicated with the Oracle database firewall together with information about the source-IP from the attacker and other information. Based upon the attack context the Oracle database firewall can be tightened in general and/or also on the specific IP from the attacker.
An additional benefit, which is in my opinion a huge benefit, is that you will be able to collect the information and logs of both the F5 firewall and the Oracle database firewall in a consolidated way. In many cases a security apartment needs to track down what happened and needs to be able to report on this and should have a trail of evidence. When multiple points of security and a multiple number of locations for logs are in place it can be very hard to track down the entire attack path and provide a consistent and correct report. Having the ability to do this from a single console is providing much more options to track and secure your vital and confidential data. When looking into securing a Oracle based solution is well worth to think about an implementation as shown above.

No comments:
Post a Comment